Getting root on a 4G LTE mobile hotspot
I have an Alcatel MW41 mobile hotspot. It works fine, but it seems to have some firmware running on it (more specifically, it’s running a web server to give you an interface to change different options), which raises two questions: 1) does it run Linux? and 2) can we get root on it?
Some research led me to find that it did, in fact, run Linux. Not only that, but there was a tool that would just give me root access to the hotspot, by the name of TCL-SWITCH-TOOL! 1 Apparently, this tool relied on the fact that the hotspot showed up as an external disk when you connect it to a computer. It did something that switched the hotspot into a debug mode, giving you a root shell.
The tool is Windows-only, but it’ll probably just work under Wine, right? I downloaded the tool, ran it, hit the “switch to debug mode” button, and….
-
The only reference I can find to this is on a Russian forum, and they don’t explain where it came from. It’s only slightly sketchy. (that link is for the MW40, but it appears to work for a number of hotspots, including the MW41) ↩
Building a period-accurate replica Soviet microcomputer
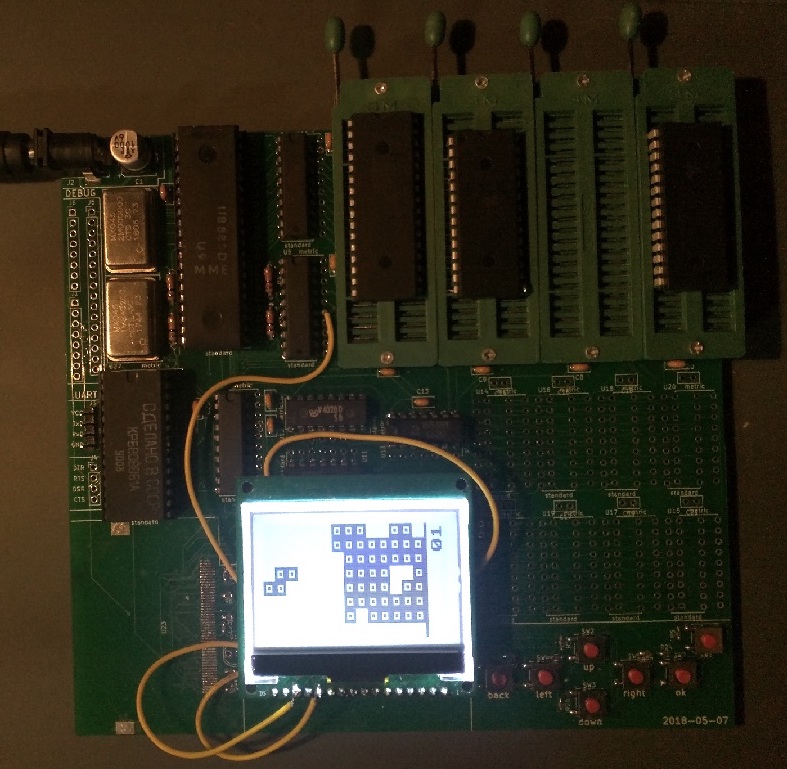
The final product.
For my 11th grade history class, our final assignment was an open-ended research project, where both the topic and the medium of presentation was up to us. Having recently watched a YouTube video about Tetris, a game invented in the Soviet Union, I instantly knew I wanted to look into computer technology in the Soviet Union during the Cold War.
However, as I begun my research, I realized that the components used at the time were still available from sites like eBay. So, I decided, instead of writing a paper, to buy some of these components and try to build a replica computer, staying as period-accurate as I reasonably could.
read more →How a malicious seed generation website stole $4 million
Update 1/29/2018: the QR code is generated by a Web Worker rather than a Service Worker as initially stated (thanks to foodblogger on Hacker News for catching this!), the publish date was corrected, and as suggested on Reddit, the article was updated to clarify how the created seeds were varied for different users, but still known to the operator of the website. You can see the original version here.
Recently, Ars Technica posted an article describing how a malicious seed generator, iotaseed.io (now offline), was able to steal almost $4 million (!) worth of IOTA from its users’ wallets. The way they describe this is that the website “stored data about each seed generated along with information about the wallet it was associated with, allowing whoever was running the site (or whoever hijacked it) to simply wait until wallets were filled and then cash them out.” This made me curious, so I decided to look into the technical details of how the scam was pulled off.
read more →